The Exploit Prediction Scoring System (EPSS) is a revolutionary tool in the realm of cybersecurity, providing a fundamentally new capability for efficient, data-driven vulnerability management. Developed by the Forum of Incident Response and Security Teams (FIRST), EPSS is a data-driven effort that uses current threat information from Common Vulnerabilities and Exposures (CVE) and real-world exploit data to predict the likelihood of a vulnerability being exploited. The website for the EPSS is: https://www.first.org/epss/
The Intricacies of the EPSS Model
The Exploit Prediction Scoring System (EPSS) model is a sophisticated tool that quantifies the likelihood of a vulnerability being exploited. It does this by generating a probability score that ranges between 0 and 1, or equivalently, 0 and 100%. A higher score signifies a greater probability that a given vulnerability will be exploited.
The computation of this score is not a simple process; it involves a comprehensive analysis of various factors. These factors include, but are not limited to, the specific characteristics of the vulnerability, the observed behavior of threat actors, and the current state of the threat landscape.
The characteristics of the vulnerability can encompass a multitude of aspects. For instance, the nature of the vulnerability (e.g., whether it allows for remote code execution or merely causes a denial of service), the software or system it affects, and the complexity required to exploit it, all play a role in determining the likelihood of its exploitation.
The behavior of threat actors is another crucial factor. This involves analyzing patterns in how and when threat actors exploit vulnerabilities. For example, threat actors may prefer to exploit certain types of vulnerabilities, or they may be more active during specific periods. Understanding these patterns can help predict which vulnerabilities are more likely to be targeted.
The current threat landscape represents the overall state of cybersecurity threats at a given time. This includes the prevalence of different types of threats, the overall level of threat activity, and emerging trends in threat behavior. The threat landscape is continuously evolving, with new threats emerging and old ones disappearing, which can influence the likelihood of a vulnerability being exploited.
What sets the EPSS model apart is its dynamic nature. The model is not static; it continually adjusts its predictions as new data becomes available. This dynamism ensures that the EPSS scores remain relevant and accurate, mirroring the fluid and ever-changing nature of cybersecurity threats.
In essence, the EPSS model is a living entity, constantly learning and adapting from the influx of new data. It reflects the current state of the threat landscape and provides a forward-looking perspective on the likelihood of a vulnerability being exploited. This makes it an invaluable tool for organizations seeking to prioritize their vulnerability management efforts effectively.
Leveraging EPSS for Enhanced Vulnerability Management
The Exploit Prediction Scoring System (EPSS) is an indispensable instrument in the toolbox of vulnerability management. It offers a data-driven methodology that aids in determining which vulnerabilities warrant immediate attention. However, it's crucial to understand the role and limitations of EPSS in the broader context of vulnerability management.
EPSS excels in estimating the probability of exploitation activity. It does this by analyzing a wealth of data, including the characteristics of the vulnerability, the behavior of threat actors, and the current threat landscape. By providing a probability score, EPSS helps organizations identify which vulnerabilities are most likely to be exploited, thereby enabling them to prioritize their remediation efforts more effectively.
However, while EPSS is a powerful tool, it should not be the sole determinant in a risk-based approach to vulnerability management. It's important to remember that EPSS is not a risk score. It does not take into account all the factors that contribute to the overall risk posed by a vulnerability.
Several other factors need to be considered when prioritizing vulnerabilities. One such factor is the accessibility of vulnerable assets to potential attackers. A vulnerability in a system that is directly accessible from the internet may pose a greater risk than a similar vulnerability in a system that is buried deep within a protected network.
The type of weakness that the vulnerability presents is another important consideration. For example, a vulnerability that allows for remote code execution may be more dangerous than one that merely causes a denial of service.
The purpose and value of the asset that is vulnerable also play a significant role in determining the overall risk. A vulnerability in a critical system that processes sensitive data may be more concerning than a similar vulnerability in a less important system.
In summary, while EPSS is a valuable tool for estimating the likelihood of a vulnerability being exploited, it is just one piece of the puzzle. A comprehensive, risk-based approach to vulnerability management should take into account a variety of factors, including but not limited to the EPSS score. By doing so, organizations can ensure that they are effectively prioritizing their resources and efforts to address the vulnerabilities that pose the greatest risk.
EPSS and CVSS: An Integrated Approach to Vulnerability Management
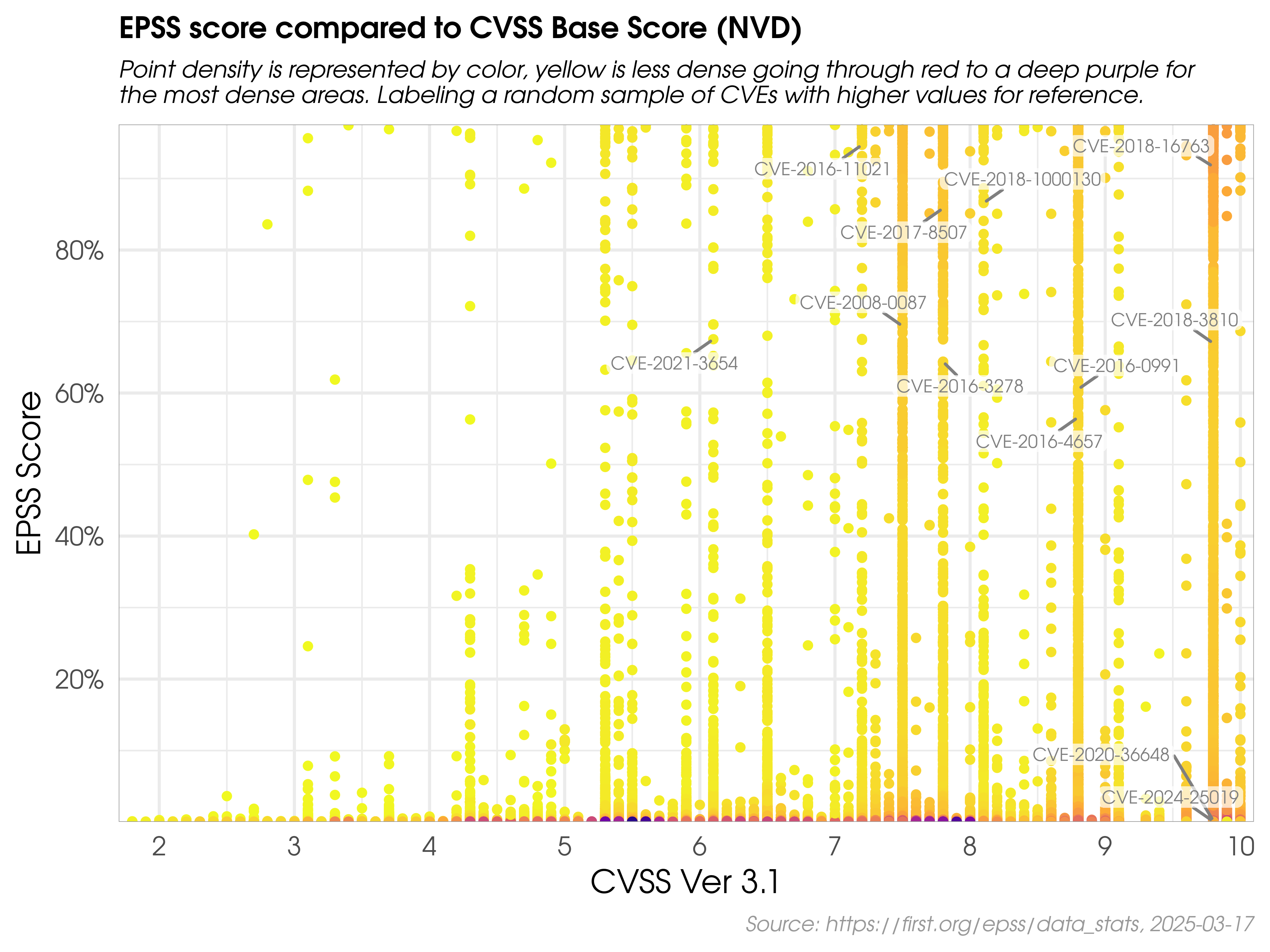
The Common Vulnerability Scoring System (CVSS) and the Exploit Prediction Scoring System (EPSS) are two distinct yet complementary tools that, when used in conjunction, can significantly enhance an organization's vulnerability management strategy.
CVSS is a universally adopted framework for assessing the severity of security vulnerabilities. It provides a standardized method for rating vulnerabilities, taking into account factors such as the complexity of the exploit, the impact on confidentiality, integrity, and availability, and whether or not user interaction is required. The result is a severity score ranging from 0 to 10, with higher scores indicating more severe vulnerabilities.
However, while CVSS is an excellent tool for assessing the potential impact of a vulnerability, it does not consider the likelihood of that vulnerability being exploited. This is a critical aspect of vulnerability management, as not all vulnerabilities are equally likely to be exploited by threat actors.
This is where EPSS comes into play. EPSS provides a probability score that estimates the likelihood of a vulnerability being exploited in the wild within the next 30 days. This score is based on a variety of factors, including the characteristics of the vulnerability, the behavior of threat actors, and the current threat landscape.
When used together, CVSS and EPSS provide a more comprehensive view of the risk posed by a vulnerability. CVSS provides insight into the potential impact of a vulnerability, while EPSS provides an estimate of the likelihood of that vulnerability being exploited. This combined perspective can help organizations better prioritize their vulnerability management efforts, focusing on the vulnerabilities that pose the greatest risk.
However, it's important to note that while there is some correlation between EPSS and CVSS scores, the relationship is not straightforward. The data suggests that attackers do not solely target vulnerabilities that have the highest CVSS scores or that are necessarily easier to exploit. This challenges the common assumption that attackers are primarily interested in the most severe vulnerabilities.
In fact, threat actors often exploit vulnerabilities that may not have the highest CVSS scores but have other attractive characteristics, such as being present in widely used software or requiring less complex exploitation techniques. This underscores the importance of using EPSS in conjunction with CVSS, as it provides a more nuanced understanding of the threat landscape and helps organizations make more informed decisions about vulnerability remediation.
EPSS in Action: A Deep Dive into Data and Statistics
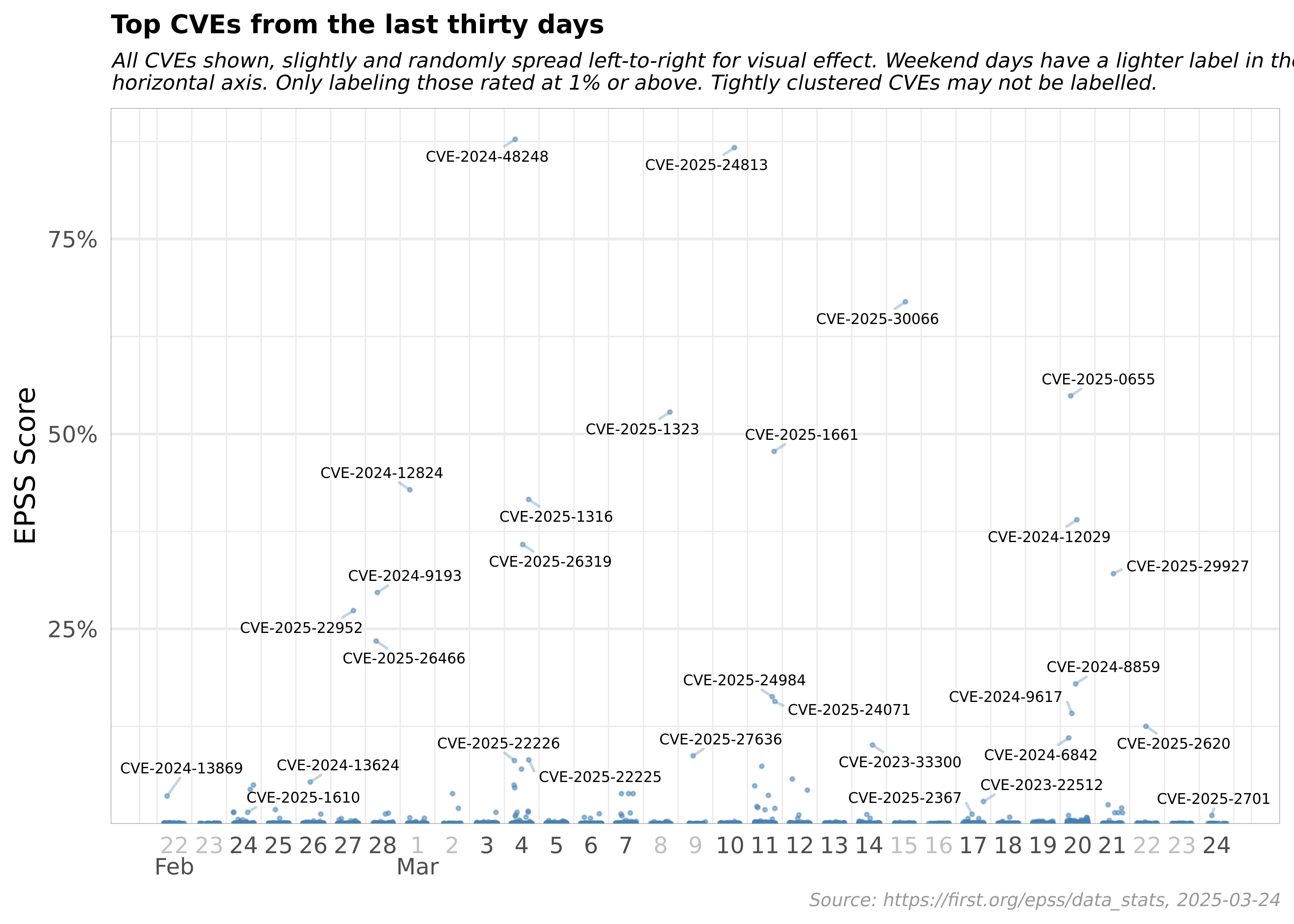
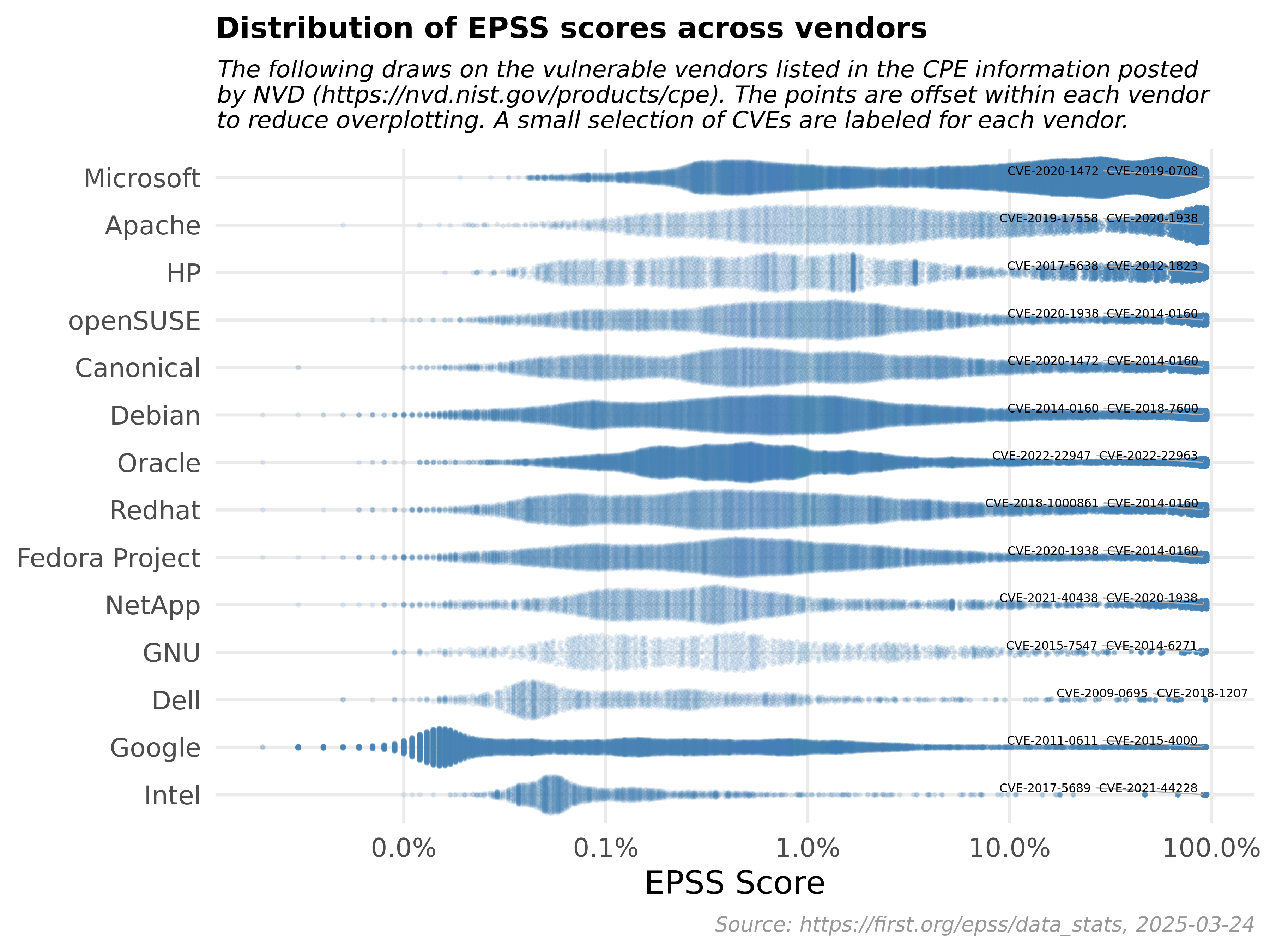
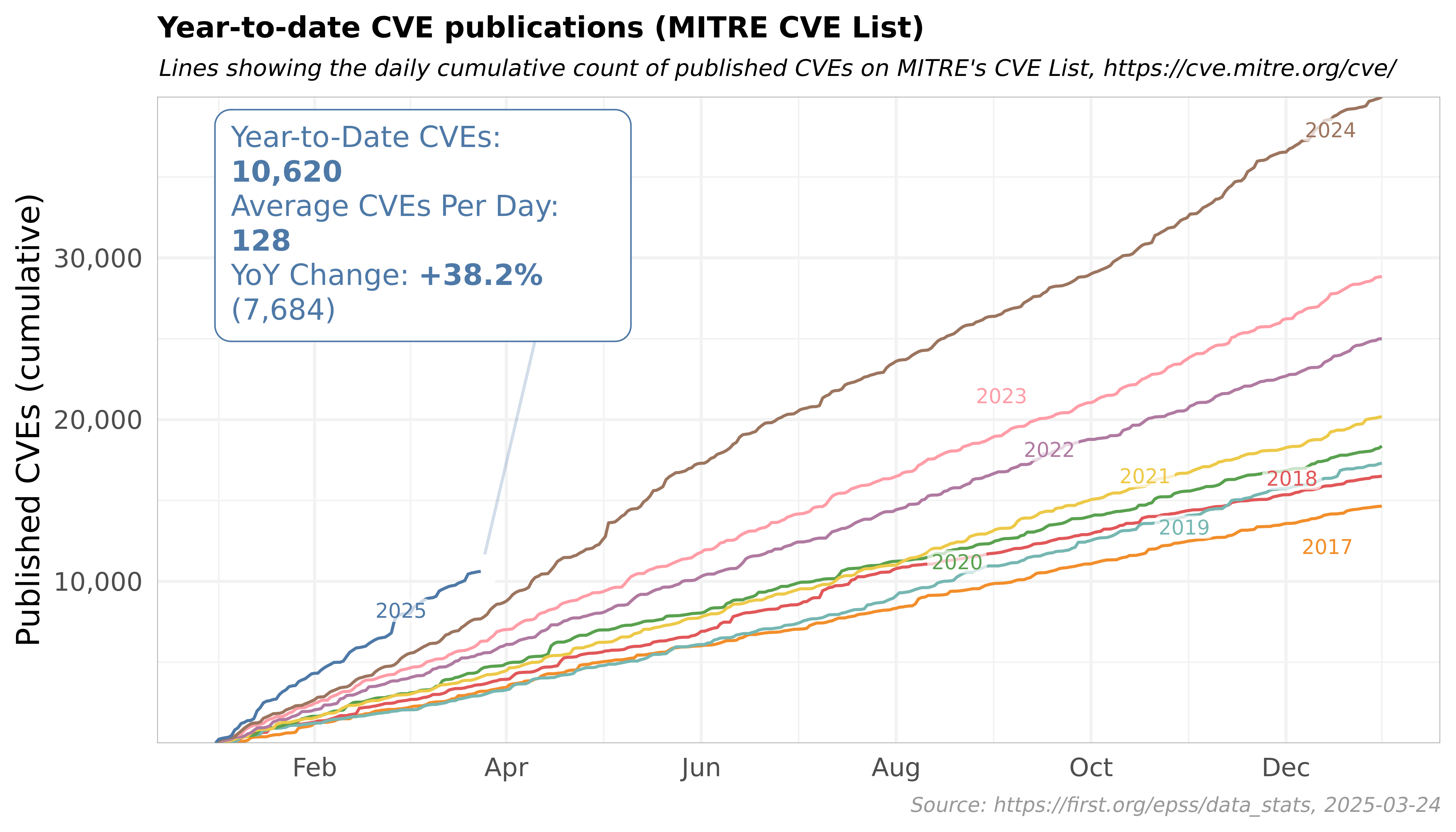
The Exploit Prediction Scoring System (EPSS) is a dynamic, data-driven model that continually evolves with the ever-changing cybersecurity landscape. As of August 3, 2023, EPSS has analyzed and scored a total of 208,754 Common Vulnerabilities and Exposures (CVEs), with 98 CVEs newly scored on this date. This vast number of scored vulnerabilities underscores the comprehensive nature of EPSS and its capacity to process and analyze extensive datasets.
The EPSS data fields provide a wealth of information about each scored vulnerability. These fields include:
CVE: This is the CVE identifier as specified by MITRE’s CVE List. Each CVE identifier is a unique reference to a specific vulnerability in the CVE database.
EPSS: This is the EPSS score, which represents the probability (ranging from 0 to 1) of the vulnerability being exploited in the wild within the next 30 days following the score's publication. This score is the heart of the EPSS model, providing a quantifiable estimate of the likelihood of exploitation.
Percentile: This represents the percentile of the current score, which is the proportion of all scored vulnerabilities with the same or a lower EPSS score. This provides a comparative measure, allowing organizations to understand how a particular vulnerability's likelihood of exploitation compares to all other scored vulnerabilities.
The data is available in a comma-separated values (CSV) format, which contains the CVE Identifier and the corresponding EPSS score as of the date the data was generated. This format allows for easy integration with other data analysis tools, enabling organizations to incorporate EPSS data into their existing vulnerability management processes.
The continuous update of EPSS scores, coupled with the detailed data fields available, empowers organizations to stay ahead of the curve in vulnerability management. By providing a data-driven estimate of the likelihood of exploitation, EPSS helps organizations prioritize their remediation efforts, focusing on the vulnerabilities that pose the greatest risk.
The following was obtained from https://www.first.org/epss/data_stats
EPSS Report for Thursday, Aug 3, 2023
- 208,754 total CVEs scored
- 98 CVEs are newly scored
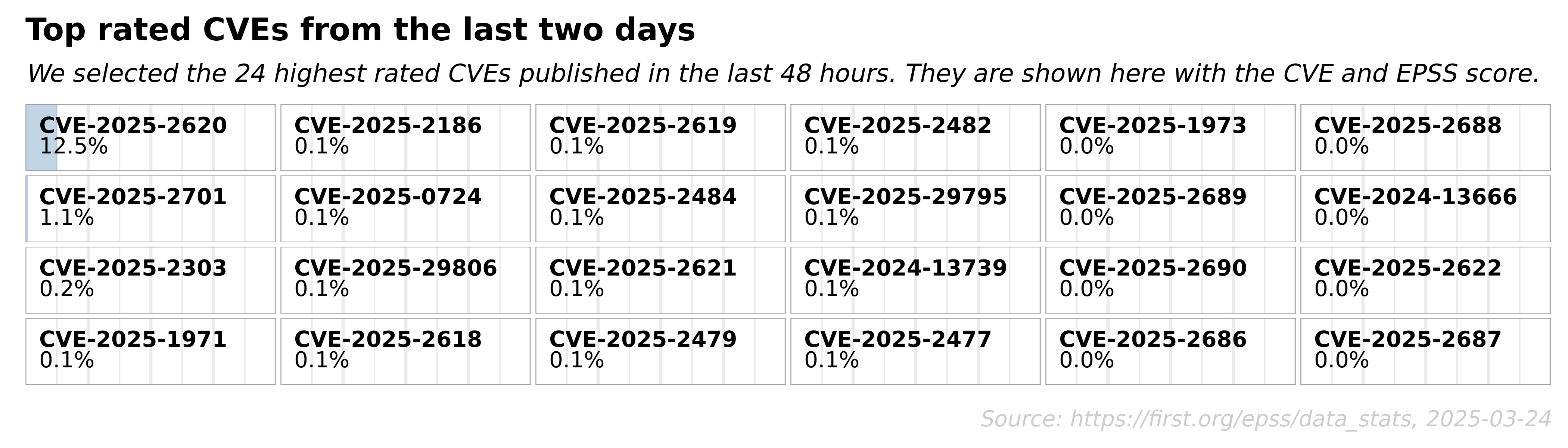
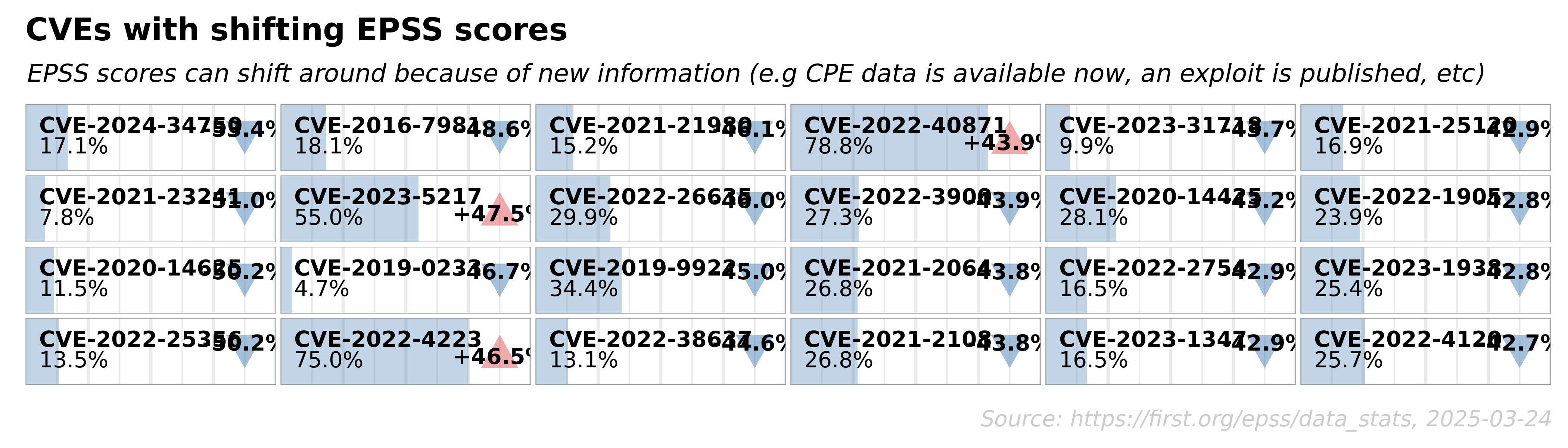
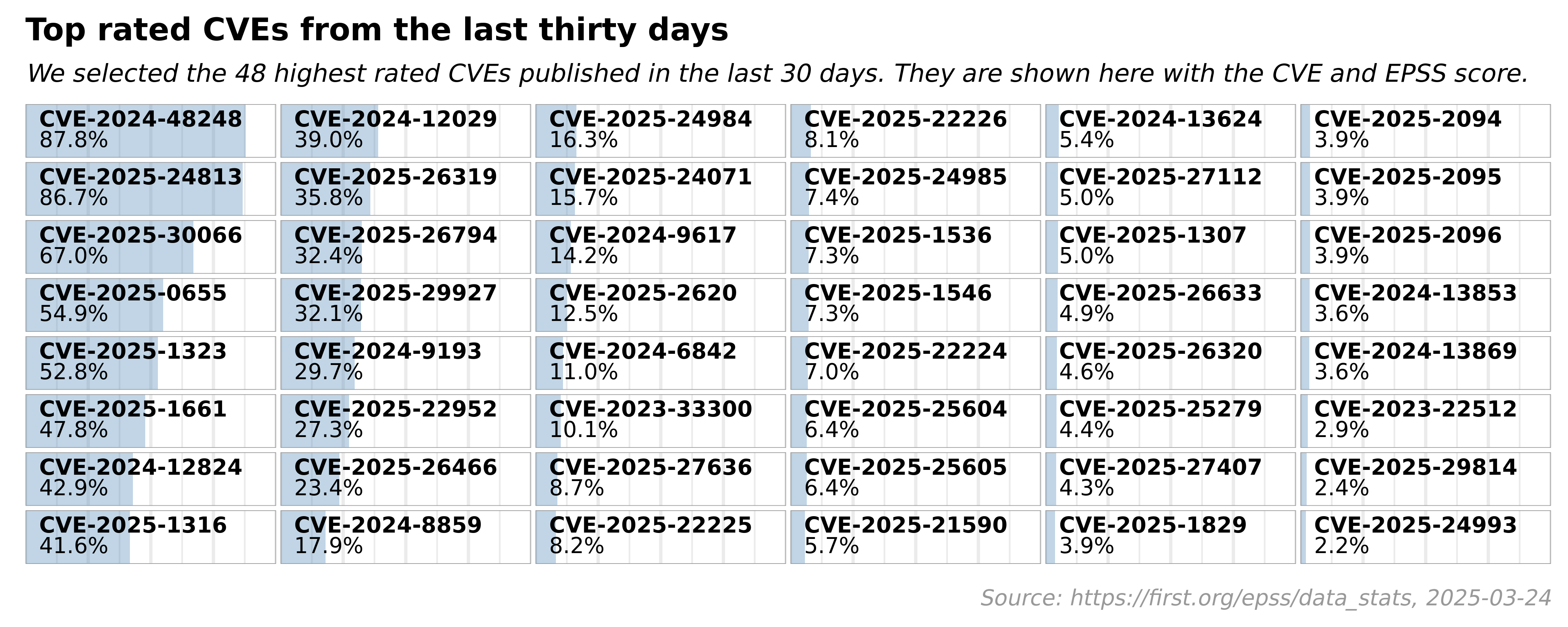
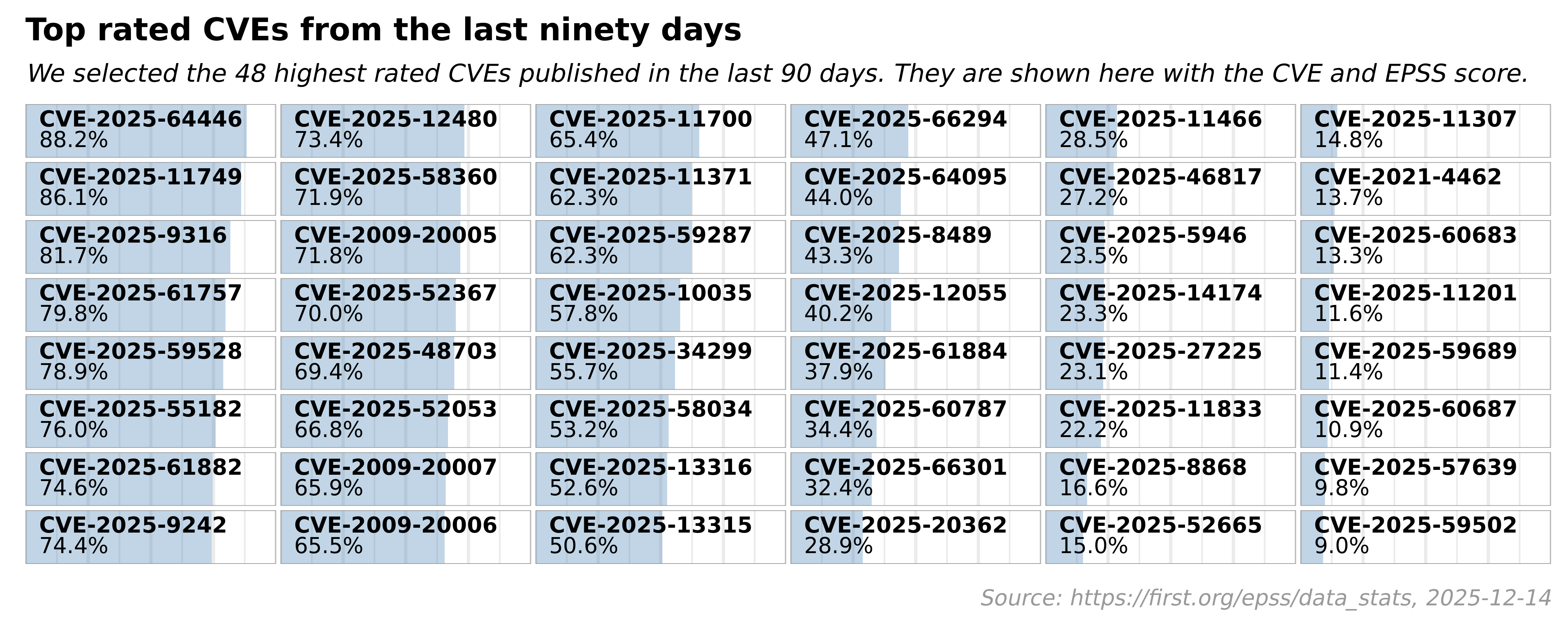
Conclusion: Harnessing the Power of EPSS for Effective Vulnerability Management
The Exploit Prediction Scoring System (EPSS) represents a significant advancement in the field of cybersecurity. By introducing a data-driven approach to vulnerability management, it equips organizations with a powerful tool to anticipate and mitigate potential threats more effectively.
EPSS operates by generating a probability score that quantifies the likelihood of a vulnerability being exploited. This score, ranging from 0 to 1, is calculated based on a multitude of factors, including the specific characteristics of the vulnerability, the behavior of threat actors, and the current state of the threat landscape. The higher the score, the greater the probability that a vulnerability will be exploited, providing organizations with a clear indication of where to focus their remediation efforts.
However, while the EPSS score is a valuable metric, it's important to understand its role within the broader context of vulnerability management. EPSS is not a risk score; it does not account for all the variables that contribute to the overall risk posed by a vulnerability. Factors such as the accessibility of vulnerable assets to attackers, the nature of the weakness the vulnerability presents, and the purpose and value of the asset in question, all play a crucial role in determining the overall risk.
Moreover, the integration of EPSS with other tools, such as the Common Vulnerability Scoring System (CVSS), can provide a more comprehensive view of the threat landscape. While CVSS assesses the potential impact of a vulnerability, EPSS estimates the likelihood of that vulnerability being exploited. This combined perspective can significantly enhance an organization's ability to prioritize vulnerabilities based on both their severity and their likelihood of exploitation.
In conclusion, the Exploit Prediction Scoring System (EPSS) is a transformative tool in the realm of cybersecurity. It brings a new level of sophistication to vulnerability management, enabling organizations to make more informed, data-driven decisions. However, it's essential to remember that EPSS is just one piece of the puzzle. A comprehensive, risk-based approach to vulnerability management should incorporate a variety of factors, including but not limited to the EPSS score. By doing so, organizations can ensure that they are effectively prioritizing their resources and efforts to address the vulnerabilities that pose the greatest risk.