From Data to Wisdom: Integrated Adaptive Cyber Defense and the Importance of Knowledge Representation & Reasoning
I. Introduction
A. Background on Integrated Adaptive Cyber Defense (IACD)
The rapid advancement of technology and the increasing interconnectedness of digital systems have led to an ever-increasing threat of cyber attacks. As the complexity and frequency of these attacks continue to rise, traditional cyber defense methods have proven to be insufficient. To address these challenges, a new approach to cybersecurity has emerged: Integrated Adaptive Cyber Defense (IACD).
IACD is a holistic approach to cybersecurity that emphasizes an integrated and adaptive response to cyber threats. It combines advanced technologies, such as artificial intelligence and automation, with human expertise to create a dynamic defense system. IACD is designed to be adaptable and flexible, allowing it to respond to the evolving threat landscape and provide effective protection against a wide range of cyber attacks.
B. Importance of IACD in today's cyber threat landscape
The current cyber threat landscape is characterized by sophisticated, persistent, and rapidly evolving attacks that can easily evade traditional security measures. These attacks can have devastating consequences, ranging from financial losses to the compromise of critical infrastructure and the loss of sensitive information.
To address these threats, there is a need for a new approach to cybersecurity that can effectively identify and respond to attacks in real-time. IACD offers a comprehensive and dynamic defense system that can detect, prevent, and respond to a wide range of cyber threats.
C. Purpose of the paper
The purpose of this paper is to explore the role of knowledge representation in IACD and its importance in enabling effective cybersecurity. The paper will provide an overview of the 4 levels of interoperability and discuss the ways in which AI and automation can be used to align data, information, knowledge, understanding, and wisdom. The paper will also provide examples of how IACD can be used to prevent and respond to cyber attacks, and how it can be implemented in organizations of various sizes and types. By the end of the paper, the reader will have a comprehensive understanding of the importance of knowledge representation in IACD and the benefits it can offer in protecting against cyber threats.
II. Data, Information, Knowledge, Understanding, and Wisdom in Cybersecurity
A. Distinctions among data, information, knowledge, understanding, and wisdom
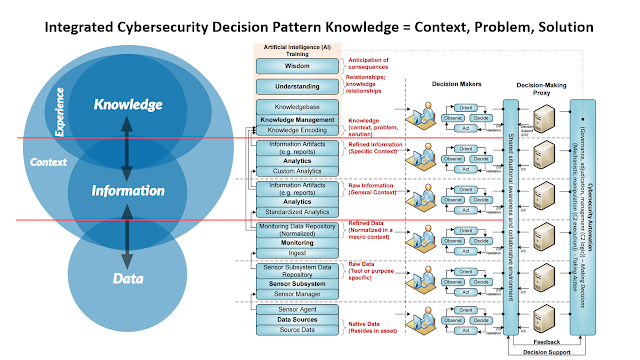
In the context of cybersecurity operations, it is important to understand the distinctions among data, information, knowledge, understanding, and wisdom. Data refers to raw material that may or may not be facts. Information is unstructured narrative that provides some context and meaning for data. Knowledge, on the other hand, is structured details that capture context, problem, and solution. Understanding captures relationships among knowledge, and essence of wisdom is the anticipation of consequences.
B. Importance of formalized knowledge representation for IACD
In the current cyber threat landscape, it is crucial to have an adaptive and integrated approach to cyber defense. Formalized knowledge representation plays a crucial role in the Integrated Adaptive Cyber Defense (IACD) by capturing, codifying, and sharing knowledge that supports cybersecurity operators and analysts' ability to perform timely agile cybersecurity operations. The formalization of knowledge provides context and facilitates assimilating new knowledge into the existing schema, making it an agile security-engineering construct to design and sustain agile cybersecurity operations.
C. Examples of different types of knowledge in cybersecurity operations
There are different types of knowledge in cybersecurity operations, including pragmatic, procedural, social, relational, conditional, and declarative knowledge. Pragmatic knowledge provides an explicit representation of best practices, such as codified organizational cybersecurity incident response details derived from actual experience. Procedural knowledge, on the other hand, is codified knowledge on security procedures, such as how to implement a firewall. Social knowledge is created by the group and involves collective planning and actions, such as specific security mechanism acquisition, implementation, and deployment. Relational knowledge, meanwhile, pertains to knowledge of people, processes, and technologies interactions to achieve the desired effect, such as a cybersecurity incident response workflow that engages multiple individuals, workgroups, and technologies. Conditional knowledge refers to knowledge of the appropriate time to employ particular security services and mechanisms, which is the essence of balancing risk mitigation with resource constraints. Finally, declarative knowledge pertains to awareness of Risk Posture and associated security services and mechanisms that comprise the Security Posture, such as the existence of anti-malware software or intrusion detection system.
The use of formalized knowledge representation in IACD helps to capture and codify these different types of knowledge, providing a foundation for the design and sustainment of agile cybersecurity operations. In the following sections, we will explore how IACD enables AI and automation through the four levels of interoperability to support cybersecurity operations.
III. Four Levels of Interoperability
A. Overview of the four levels of interoperability in IACD
Integrated Adaptive Cyber Defense (IACD) is an approach to cyber defense that involves the use of advanced technologies such as artificial intelligence (AI) and automation to detect, prevent, and respond to cyber threats in real-time. IACD relies on four levels of interoperability that enable different systems, applications, and devices to work together seamlessly to improve an organization's overall cybersecurity posture. The four levels of interoperability are:
- Foundational Interoperability: At this level, the focus is on establishing interconnectivity between different systems and applications, enabling them to securely communicate and exchange data. This level is the foundation upon which all subsequent levels of interoperability are built, and it enables basic data exchange services.
- Structural Interoperability: At the structural level of interoperability, the focus shifts to the format, syntax, and organization of data exchange, including at the data field level for interpretation. This level is concerned with the packaging of data via message format standards, and it provides the structure that developers need to write code to work with the data in their applications or systems.
- Semantic Interoperability: At the semantic level of interoperability, the focus is on creating a common vocabulary that enables accurate and reliable machine-to-machine communication across information silos. This level provides for common underlying models and codification of the data, including the use of data elements with standardized definitions from publicly available vocabularies, providing shared understanding and meaning to the user.
- Organizational Interoperability: At the organizational level of interoperability, the focus is on governance, policy, social, legal, and organizational considerations to facilitate the secure, seamless and timely communication and use of data both within and between organizations, entities, and individuals. This level enables shared consent, trust, and integrated end-user processes and workflows.
B. Level 1: Foundational Interoperability
At Level 1, the focus is on establishing interconnectivity between different systems and applications, enabling them to securely communicate and exchange data. This level is the foundation upon which all subsequent levels of interoperability are built, and it enables basic data exchange services.
Cybersecurity examples of AI and automation in Level 1 include security orchestrators and standardized APIs for controlling sensors and actuators. Data Science, Analytics, and Machine Learning are also enabled at this level, allowing organizations to analyze large volumes of data from different sources and identify patterns, detect anomalies, and gain insights that can inform their security strategies.
For example, machine learning algorithms can be used to detect and block spam emails, identify potential network breaches, and flag suspicious activities. The use of automation and AI at this level enables organizations to detect and respond to threats in real-time, improving their overall cybersecurity posture.
C. Level 2: Structural Interoperability
At Level 2, the focus shifts to the format, syntax, and organization of data exchange, including at the data field level for interpretation. This level is concerned with the packaging of data via message format standards, and it provides the structure that developers need to write code to work with the data in their applications or systems.
Cybersecurity examples of AI and automation in Level 2 include robot process automation (RPA) and AI at the edge, where analytics and machine learning are performed on devices or sensors directly, without relying on a centralized analytic or machine learning stack. This enables organizations to process and analyze data more efficiently, improving their ability to detect and respond to threats in real-time.
Data Science, Analytics, Machine Learning, and Deep Learning are also enabled at this level, allowing organizations to gain deeper insights into their data and make more informed decisions. For example, organizations can use machine learning algorithms to analyze log data, detect anomalies in network traffic, and predict future threats.
C. Level 3: Semantic Interoperability
At the semantic level of interoperability, the focus is on creating a common vocabulary that enables accurate and reliable machine-to-machine communication across information silos. This level provides for common underlying models and codification of the data, including the use of data elements with standardized definitions from publicly available vocabularies, providing shared understanding and meaning to the user.
Semantic interoperability is about providing common underlying models and codification of the data. This means that data can be exchanged with unambiguous, shared meaning, which allows the receiving system to interpret the data. For instance, the use of data elements with standardized definitions from publicly available vocabularies can provide shared understanding and meaning to the user. AI and automation at this level involve using knowledge engineering to create a knowledge-based system with normalized virtual representations, called ontologies, of enterprise information silos. For example, an ontology can be created to represent the different types of cyber threats that an organization may face, including their characteristics and potential impact. This enables knowledge-driven automation use cases, such as automatically identifying and mitigating threats based on the ontology.
At this level, Knowledge Representation and Reasoning, Machine Reasoning, and Expert Systems are enabled. These technologies provide a higher level of automation by enabling systems to automatically reason about data and make decisions based on that reasoning. For example, organizations can use expert systems to automatically triage security alerts, identify the root cause of security incidents, and recommend appropriate responses with full transparency and explainability thanks to knowledge representation and logical reasoning.
D. Level 4: Organizational Interoperability
At the organizational level of interoperability, the focus is on governance, policy, social, legal, and organizational considerations to facilitate the secure, seamless, and timely communication and use of data both within and between organizations, entities, and individuals. This level enables shared consent, trust, and integrated end-user processes and workflows.
At this level, AI and automation can be used to encode organizational knowledge, organizational context, and human expertise in applying organizational processes and workflows to create an AI Expert System on top of the knowledge-based system for knowledge-driven automation across the organization. These technologies enable organizations to automate complex workflows and decision-making processes, reducing the risk of human error and improving the overall efficiency of the organization's cybersecurity operations.
Examples of AI and automation at this level include the use of natural language processing (NLP) mapped to the ontologies created by knowledge representation to analyze policy documents and extract key concepts, which can be used to develop and implement cybersecurity policies and procedures. Another example is the use of machine learning on top of the knowledge representations to analyze user behavior data to identify potential security risks and suggest improvements to security training and awareness programs. This is really where composite AI will thrive from the increased level of interoperability. In composite AI, machine learning and machine reasoning are combined, working from the same formal knowledge representations where the underlying integrated data is mapped to.
Overall, the four levels of interoperability in IACD are critical for enabling effective cybersecurity operations in today's rapidly evolving threat landscape. By leveraging the power of AI and automation at each level, organizations can enhance their situational awareness, streamline their incident response processes, and better protect themselves against advanced threats.
IV. AI and Automation in IACD
A. Overview of AI and automation in IACD
As cyber threats continue to evolve, it becomes increasingly challenging for organizations to keep their networks and systems secure. Integrated Adaptive Cyber Defense (IACD) leverages AI and automation to provide a more effective and efficient approach to cybersecurity. AI and automation can be aligned to different levels of knowledge, ranging from data to wisdom. At the data level, AI and automation can collect and analyze large volumes of data to identify patterns and anomalies that may indicate potential threats. At the knowledge level, AI and automation can use formalized knowledge representation to identify and mitigate threats, and at the wisdom level, AI and automation can automate complex decision-making processes.
The benefits of AI and automation in IACD are numerous, including the ability to detect and respond to threats more quickly, reduce the risk of human error, and improve the overall efficiency of cybersecurity operations. By automating repetitive tasks and using AI algorithms to analyze large volumes of data, organizations can free up their security teams to focus on more strategic initiatives.
B. Examples of different fields of AI that align with different levels of data, information, knowledge, understanding, and wisdom:
Data:
- Machine learning: Used for analyzing and identifying patterns in large data sets, including data obtained from sensors and IoT devices.
- Natural language processing (NLP): Used for processing unstructured data, such as text data and speech data, to extract information.
- Computer vision: Used for analyzing image and video data, including identifying objects and tracking movements.
Information:
- Rule-based systems: Used for automating decision-making based on a set of rules and if-then statements.
- Bayesian networks: Used for probabilistic reasoning and decision-making based on a set of interconnected variables.
- Fuzzy logic: Used for dealing with uncertain and imprecise data.
Knowledge:
- Knowledge representation and reasoning: Used for representing knowledge in a structured way and making logical inferences based on that knowledge.
- Expert systems: Used for automating decision-making based on human expertise and knowledge.
- Case-based reasoning: Used for problem-solving based on past experiences and cases.
Understanding:
- Deep learning: Used for processing and analyzing complex data sets, including speech, text, and image data, to extract meaning and identify patterns.
- Cognitive computing: Used for mimicking human thought processes to analyze and interpret complex data sets.
- Knowledge representation and reasoning: Used to create a knowledge-based system with normalized virtual representations, called ontologies, of enterprise information silos to provide a common vocabulary that enables accurate and reliable machine-to-machine communication across information silos, and allows systems to automatically reason about data and make decisions based on that reasoning.
- Machine reasoning: Enables systems to automatically reason about data and make decisions based on that reasoning. This technology provides a higher level of automation, allowing organizations to automate complex workflows and decision-making processes, reducing the risk of human error, and improving the overall efficiency of the organization's cybersecurity operations.
- Expert systems: Can be used to automatically triage security alerts, identify the root cause of security incidents, and recommend appropriate responses, allowing organizations to gain a higher level of automation and reduce the risk of human error in their cybersecurity operations.
Wisdom:
- Machine reasoning: Used for making decisions based on multiple sources of information and reasoning over multiple levels of abstraction.
- Context-aware computing: Used for making decisions based on situational context, including time, location, and user preferences.
- Autonomous agents: Used for making decisions and taking actions based on learned behavior and interactions with the environment.
Knowledge representation and reasoning, machine reasoning, and expert systems are all AI technologies that align with knowledge and understanding. These technologies enable systems to reason about data and make decisions based on that reasoning, and to automate decision-making based on human expertise and knowledge. For example, an expert system can be used to automatically triage security alerts, identify the root cause of security incidents, and recommend appropriate responses based on the knowledge representation and reasoning. Similarly, machine reasoning can be used to make decisions based on multiple sources of information and reasoning over multiple levels of abstraction, such as determining the best course of action to respond to a security incident.
C. Cybersecurity examples of AI and automation in data collection and analysis
One of the key benefits of AI and automation in IACD is their ability to collect and analyze large volumes of data to identify potential threats. Examples of AI and automation in data collection and analysis include:
- Automated threat detection and response: AI and automation can be used to detect potential threats and respond to them in real-time. For example, an AI system can automatically block an IP address that is attempting to launch a denial of service attack.
- Automated log analysis and management: AI and automation can be used to analyze logs from multiple sources to identify potential threats. For example, an AI system can be used to analyze logs from firewalls, intrusion detection systems, and other security devices to identify patterns that may indicate a potential attack.
D. Cybersecurity examples of AI and automation in decision-making
AI and automation can also be used to automate decision-making processes in IACD. Examples of AI and automation in decision-making include:
- Automated incident response: AI and automation can be used to respond to security incidents in real-time. For example, an AI system can automatically quarantine a device that is suspected of being infected with malware.
- Automated risk assessment and management: AI and automation can be used to assess the risk associated with different security threats and prioritize the response based on the level of risk.
E. Cybersecurity examples of AI and automation in action
AI and automation can also be used to automate a range of cybersecurity actions, including:
- Automated patch management and system updates: AI and automation can be used to automatically update software and systems to ensure that they are protected against known vulnerabilities.
- Automated network configuration and maintenance: AI and automation can be used to automatically configure and maintain network devices, such as firewalls and routers, to ensure that they are operating efficiently and effectively.
V. Conclusion
A. Summary of the main points discussed in the paper
In this paper, we have discussed the importance of integrated adaptive cyber defense (IACD) and the role of AI and automation in enabling IACD. We have also examined the distinction between data, information, knowledge, understanding, and wisdom in the context of cybersecurity operations and the importance of formalized knowledge representation for IACD. Additionally, we have explored the four levels of interoperability in IACD and provided examples of cybersecurity applications of AI and automation at each level.
B. Implications of IACD for the future of cybersecurity
The increasing complexity and sophistication of cyber threats require a more advanced and adaptive approach to cyber defense. IACD provides a framework for addressing these challenges by enabling seamless communication and integration of different cybersecurity systems and processes. The use of AI and automation in IACD enables faster and more accurate detection, response, and decision-making in the face of rapidly evolving cyber threats.
C. Areas for future research and development in IACD and AI/automation in cybersecurity
As the cyber threat landscape continues to evolve, there is a need for ongoing research and development in IACD and AI/automation in cybersecurity. Specifically, future work should focus on the development of more advanced AI and automation technologies that can better address the complex and dynamic nature of cyber threats. Additionally, there is a need for continued development and refinement of knowledge representation and reasoning techniques to support more effective decision-making in IACD. Finally, research efforts should focus on the development of more advanced and effective methods for integrating different cybersecurity systems and processes, enabling more seamless and efficient communication and collaboration between these systems.
.PNG)